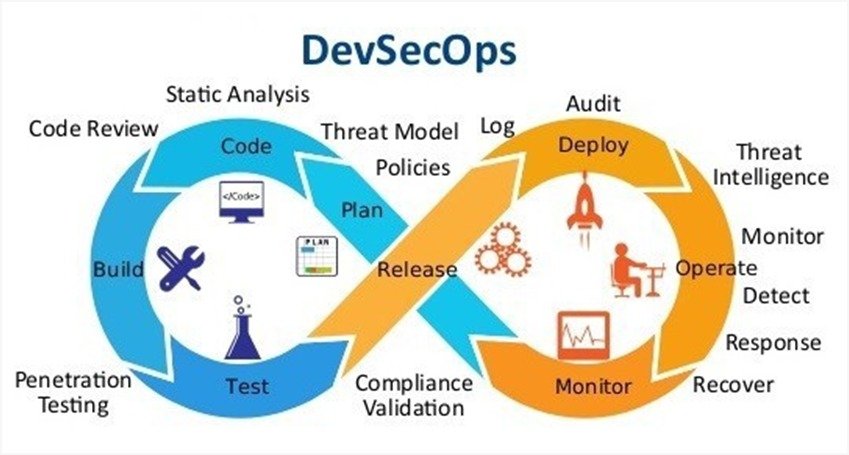
Our most valuable assets at Sceptre Consulting are our clients and workers, who we take great care of. We uphold a clan organizational culture in which each person has an equal chance for development, exposure, and care. We respect our staff, offer a work-life balance, and help them advance in their careers.
Phone No.
+353-892536644
info@sceptreconsultancy.com